ZKX Helix:
Protect with Pinpoint Accuracy.
A security framework is only as strong as its policy. Policy is the backbone upon which security operates and serves one critical function: tying technology to action. Whether organizational or access, Policy is responsible for securely deploying, accessing, and maintaining the network.
Helix Key Benefits:
- Adaptable to any standardized framework, including commercial, federal, and military systems
- Enterprise policies flow seamlessly to the tactical edge or to federated partners
- Granular, flexible, and customizable access policies protect your network with unparalleled precision
- Build access policies from the identity attributes of your existing users and their devices
Granular, Flexible, and Highly Customizable
Helix can be fine-tuned to your organization’s specific policy needs. Whatever your security environment requires – be it end-to-end encryption, the latest communication protocol, or post-quantum cryptography – can be configured with Helix.
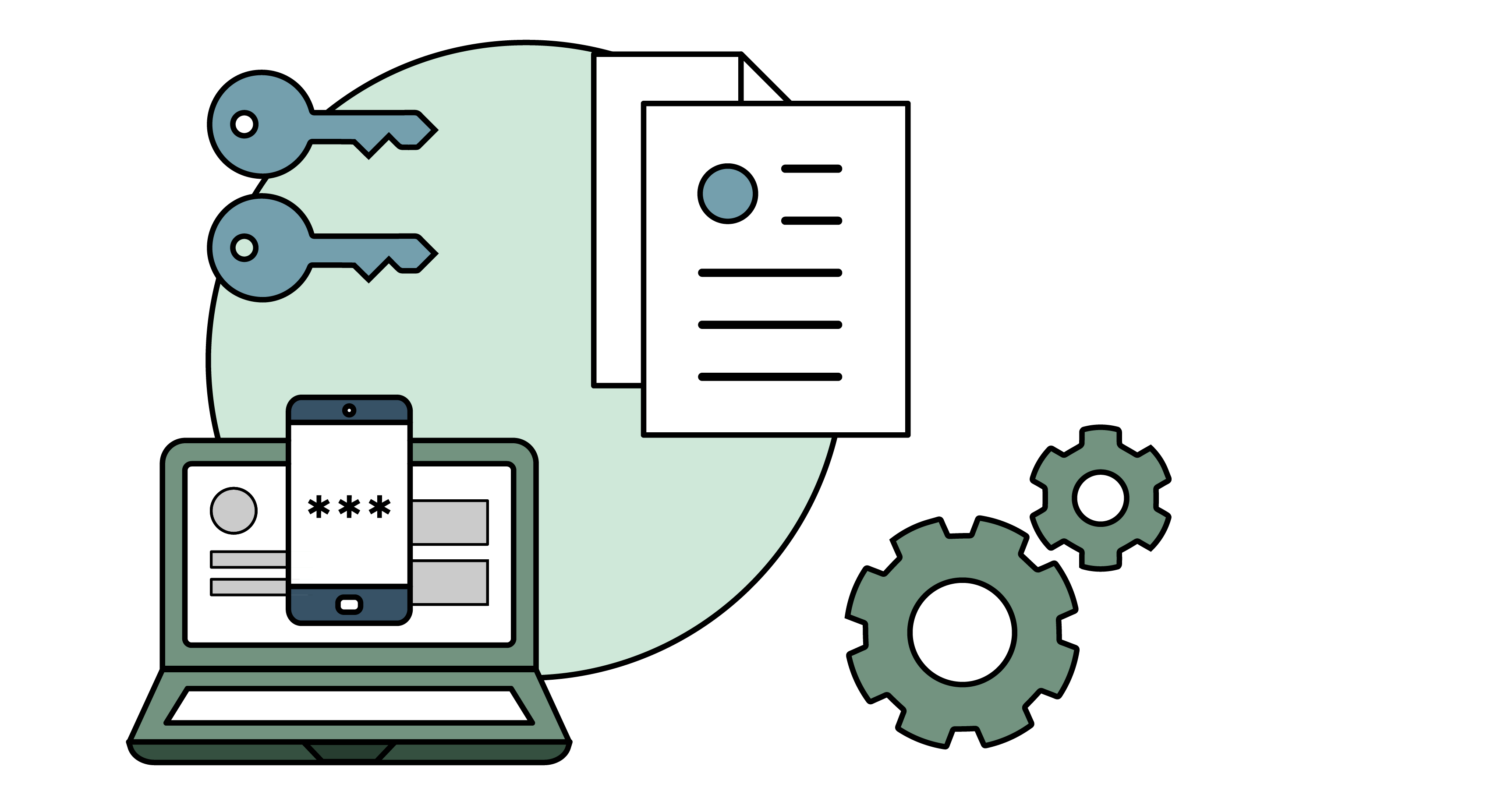
In Helix, network administrators can define access policies on the basis of identity attributes, characteristics native to your users, their roles in your organization, and the devices they use.
Policy enforcement in Helix is dynamic. If the parameters of an access policy change, Helix MFA enforces them in real-time.
These access policies are enforced on the basis of three parameters:
- Device identity
- Authentication artifacts
- Confidence score
Policy enforcement at the Edge
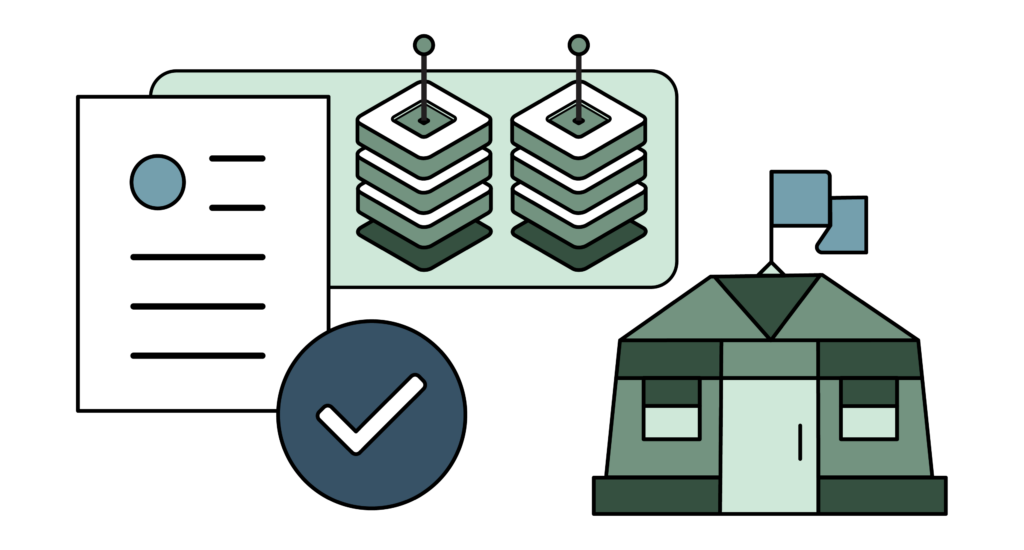
Helix enables your organization’s enterprise policies to follow you in tactical or forward-deployed situations. It can even extend past your network’s boundaries to that of the networks of your federated mission-partners.
Because MFA and policy enforcement for ZKX Helix are driven almost exclusively by publicly available data, users and devices that don’t natively belong to your networked ecosystem can enter your network and have your access policies enforced upon them – even if you didn’t enroll them, their devices, or provision them any specific equipment.
This flexible and powerful characteristic exclusive to the Helix platform ensures that need-to-know is always enforced on your network – even in situations when multiple organizations meld together, network conditions are changing all the time, and dedicated backhauls to larger enterprise structures are denied or intermittent.