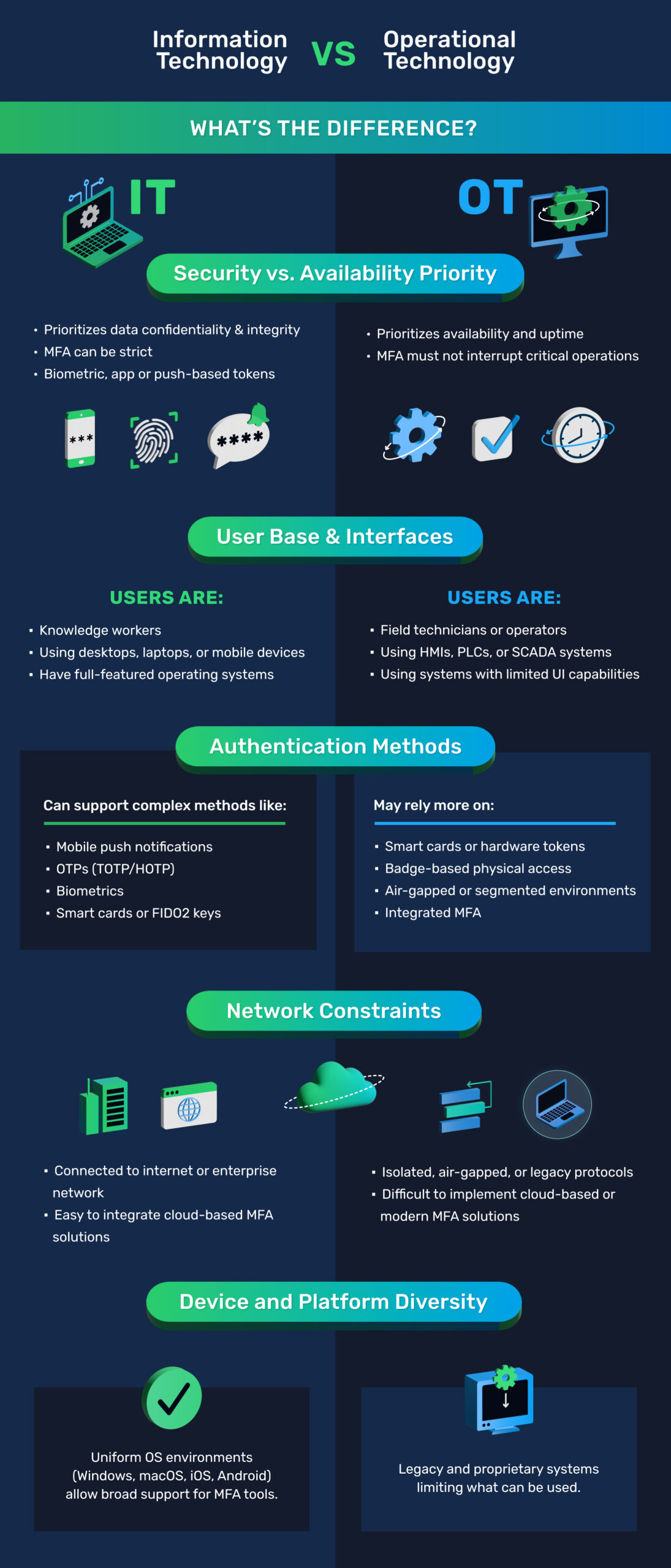
Multi-factor authentication (MFA) is one of the most effective ways to secure systems against unauthorized access. In the world of IT, MFA is often straightforward. Users confirm their identity with app-based prompts, biometric scans, or one-time codes, usually on well-connected, modern devices. But when you move into the world of operational technology (OT), things get more complicated, requiring a more nuanced approach.
Different Priorities: Security vs. Uptime
IT environments prioritize data confidentiality and integrity. Here, users can afford a strict MFA process involving biometrics, push notifications, or authenticator apps. OT environments, however, must prioritize availability and uptime. These systems often control critical infrastructure like power plants or manufacturing lines, where even a brief interruption due to MFA delays can have serious consequences. MFA in OT must be seamless, non-intrusive, and fast.
Different Users, Different Needs
IT users are typically office workers using laptops, desktops, or smartphones with rich user interfaces that easily support modern MFA tools. In OT, users are often field technicians or operators working with specialized hardware like HMIs, PLCs, or SCADA systems — devices that may have limited or legacy interfaces. These constraints require authentication methods that integrate smoothly without disrupting operations.
Tailored Authentication Methods
IT environments can leverage a broad range of MFA methods: mobile push notifications, time-based one-time passwords (TOTP), biometrics, smart cards, and FIDO2 keys. OT environments often depend on hardware tokens, badge-based access, or MFA embedded directly into industrial access controls. Many OT networks are air-gapped or segmented, limiting cloud-based MFA options.
Infrastructure and Platform Constraints
IT networks are generally connected to the internet or enterprise systems, allowing seamless integration of cloud-based MFA. OT networks, by contrast, often rely on legacy protocols, proprietary systems, or complete air gaps. This makes implementing modern MFA more challenging, requiring specialized solutions that don’t disrupt critical processes.
ZKX Solutions: Bridging the Gap Between IT and OT
At ZKX Solutions, we understand these critical differences, and our authentication platform is specifically designed to handle both IT and OT environments. Helix delivers flexible, precise, and secure multi-factor authentication tailored to the unique priorities and constraints of each environment. Whether you need stringent, layered security in IT or rapid, non-disruptive authentication in OT, Helix adapts — giving you comprehensive protection without compromise.