People often link security and encryption together. While they go hand in hand, they are in fact two entirely different concepts. Security is all about protecting data and information, while encryption is just one of the means of accomplishing this.
Security
When asked to describe security or secure communications, we tend to dive right into a discussion of encryption. We’ll talk about the protocols, ciphers, interfaces, and methods to achieve a strongly encrypted session. A properly encrypted session, however, is meaningless if a malicious actor should infiltrate the network and gain access to the session controller. Maybe doing so will provide the malicious actor access to the session media before it is encrypted. Or perhaps the goal is simply to disrupt the service and prevent any communications. While encryption plays a key role in security, it is not the entire story.
The bottom line is encryption is part of what makes up security; security does not make up encryption. When it comes to security, there are many tools at your disposal beyond encryption, such as cybersecurity policy and culture.
Encryption
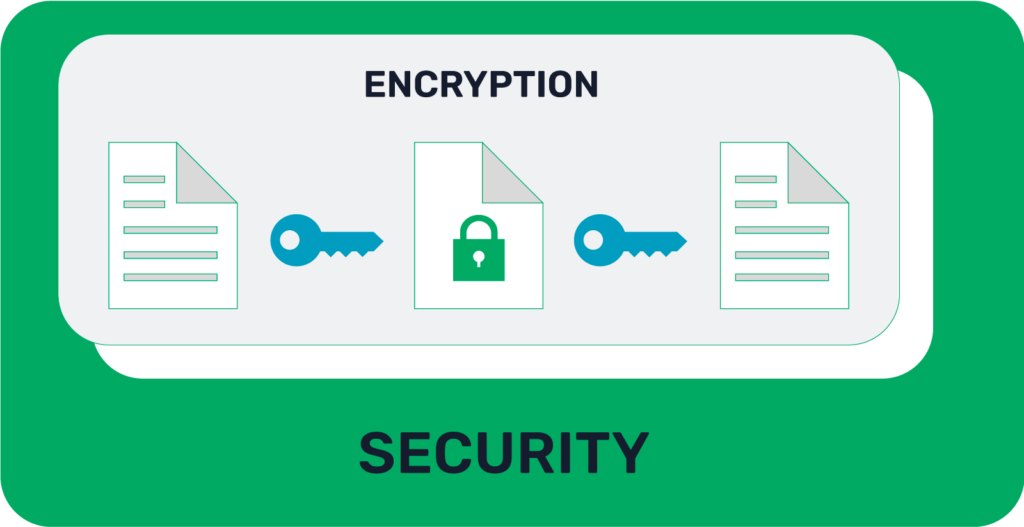
Encryption is the act of using a cipher (algorithm) and key (variable data) to encode information. Only those that know the cipher and have access to the appropriate key can decode the information. Common examples of encryption protocols and methods are the Transport Layer Security (TLS) protocol, Secure Shell (SSH), Advanced Encryption Standard (AES), and Elliptic Curve Cryptography (ECC).
Conclusion
In short, security is the combination of technical and human factors which, taken together, decrease the risk of unauthorized access or use of information. Security is the overarching umbrella and encryption is simply one part of it. Encryption is how information or data is converted to a secret language to not be compromised. Encryption is just one way to boost security.
ZKX Solutions has not reinvented cryptography. Instead, we are using proven cryptographic functions to achieve novel operational security in the context of multifactor authentication (MFA). ZKX is driven by zero-knowledge proofs (ZKPs) and is agnostic to the application, transport, endpoints, artifacts, policies, and network you already have in place. Authenticating secrets are split between what the human user will be expected to reproduce (e.g., password, PIN, RFID tag, etc.) and cryptographic data that resides on the device they have enrolled with. By themselves, these secret fragments are not enough to compromise any sensitive information about a Prover or their private authenticators.
For more information on how ZKX works or how ZKX can help secure your network reach out to collin@ZKXsolutions.com.