As technology evolves and systems become more distributed across various environments, the complexities of managing and securing digital assets have significantly increased. A fundamental strategy in the field of cybersecurity is to enforce the principle of least privilege, which means that each user or service account should only have the minimal access rights necessary to perform their specific tasks. This approach discourages granting extensive permissions simply for convenience or to address immediate concerns.
What is Identity and Access Management (IAM)?
Identity and Access Management, commonly abbreviated as IAM, encompasses the processes and technologies that manage who can authenticate (log in) and what they are authorized to do once granted access. This fine-grained management of permissions, enables organizations to specify exactly which resources can be accessed and what actions can be performed on those resources by each individual user or service account.
To illustrate this concept further, consider the use of IAM in the context of Amazon Web Services (AWS) and its Simple Storage Service (S3). Here, an S3 bucket serves as a cloud storage solution for various files. A sample IAM policy for controlling actions related to this S3 bucket might be structured as follows:
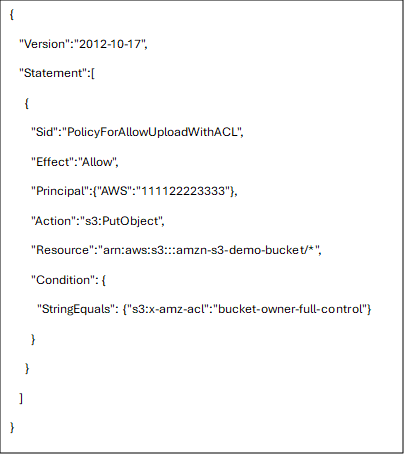
This policy grants the specified user the permission to perform the action “s3:PutObject,” effectively allowing them to upload files to a designated resource identified by the Amazon Resource Name (ARN): “arn:aws:s3:::amzn-s3-demo-bucket.” If this policy were altered to include the effect “Deny,” the user would be restricted from uploading any files to this specific bucket. This example highlights the power of fine-grained access control, which can be tailored even further to restrict access to specific directories within the bucket.
Effective IAM implementation can substantially reduce the risk exposure of resources, thus limiting the potential advantages available to adversaries in the event of a security breach. For example, if an account with this policy were compromised, the only action an attacker could execute—assuming this was the sole policy operational—would be to upload files to the “amzn-s3-demo-bucket.” This containment minimizes the damage an attacker can inflict.
How does ZKX Helix handle IAM?
ZKX Helix operates without a traditional IAM framework; however, it employs a structured policies system that delineates specific access rights and actions permitted for users. Each policy functions as a comprehensive guide, detailing what each user can access and how they can interact with those resources.
To enhance security, ZKX Helix implements varying levels of security checks that are contingent upon the security classification assigned to each policy. These checks can range from basic requirements, such as entering a passcode, to more sophisticated authentication methods like a Common Access Card (CAC). As the security requirements increase, users may face more rigorous verification processes, ensuring that sensitive data and resources remain protected against unauthorized access.
Contact us to schedule a demo
ZKX Solutions is looking for a partner to implement our patented zero-knowledge proof solution. If you would like to learn more about ZKX Helix, contact us today to schedule a demo that includes how Helix can be tailored to fit your organizations access control requirements.