Zero Knowledge and Zero Trust: they’re basically the same, right? Not quite.
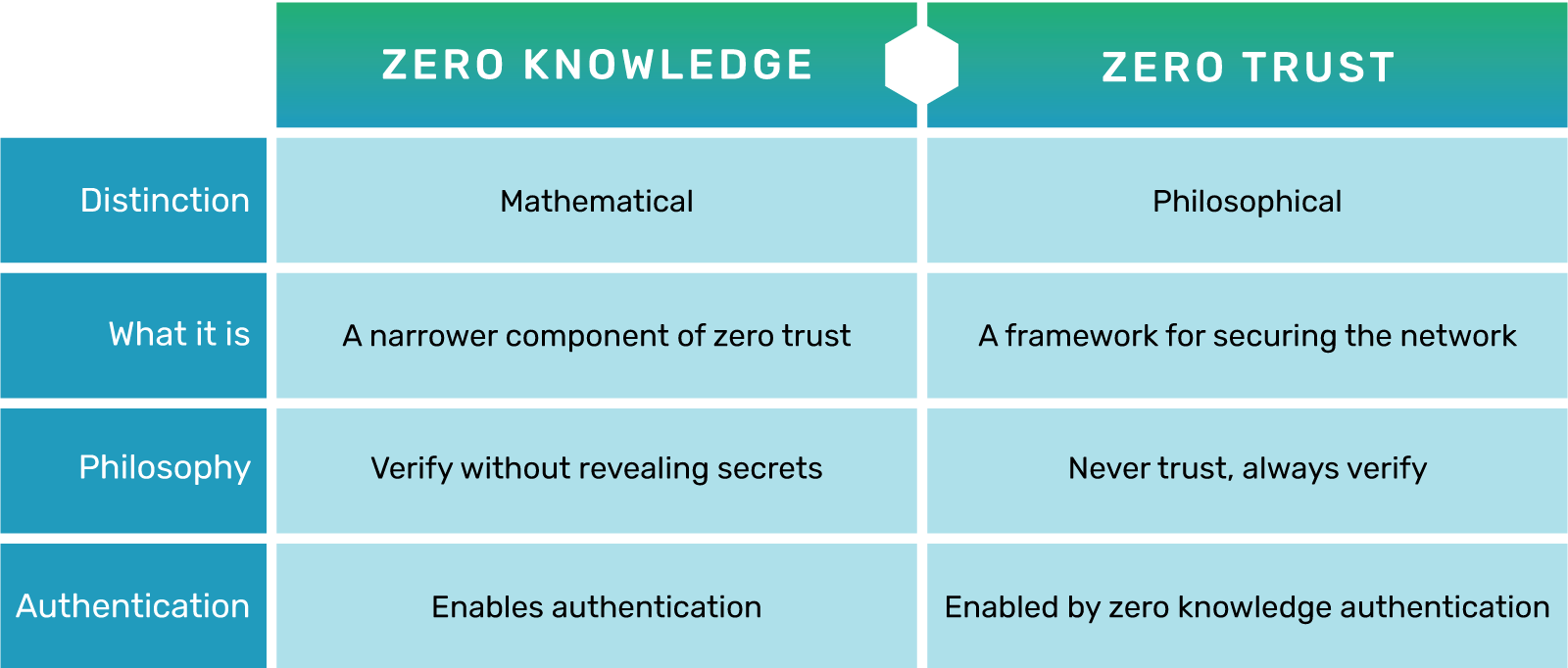
While these two terms might be similar in name, they are in fact two completely different ideas. Zero Knowledge can be used to help complete the notion of Zero Trust, but it cannot work in the opposite direction. Zero Knowledge is a mathematical distinction, whereas Zero Trust is a philosophical one.
As cyber threats continue to advance, the current network model is only becoming more insufficient in protecting critical data. In more classical network models, once you enter the network you have the authorization to access privileged data within said network. This compromises critical information, as we have seen in some of the most infamous cyber-attacks and breaches. This is where the concept of Zero Trust comes into play.
Zero Trust
Zero Trust is built on the idea that trust does not exist within the scope of cyber operations – be it between a network and its users, a network and its architectural components, or a user base and their organization. Architecturally, there is the assumption that there is no perimeter on the network and thus all data needs to be protected as though they are already exposed. Every point within the network would constantly require some form of authentication to access the data behind it.
Zero Knowledge
Zero Knowledge can be viewed as a narrower component of Zero Trust. Zero Knowledge enables specific actions like authentication that can be completed without sacrificing valuable secret or identifying information. This smaller slice of security further protects personal data like PII by no longer risking its exposure, as it is never stored or transmitted when used for authentication. Under this model, data associated with an item can be used for authentication that alone would be invaluable instead of using personal data that could be stolen. This model works under the assumption that each user or device was already compromised. By authenticating not only the user but the device as well, an extra layer of protection is added while minimizing computational or communicative overhead.
ZKX
The ZKX Engine offers seamless and frictionless multi-factor authentication designed to embody the foundational principles of zero trust. The ZKX Engine is designed atop a foundation of zero-knowledge proofs — longstanding mathematical functions which are used to prove one’s knowledge of secret information without revealing what that secret information is. The benefits of the ZKX Engine are:
- Protects personal data by not storing personal information
- No data is at risk if the endpoint device is compromised
- Interoperable with various network mediums such as satellite, RF radio frequency, and IP networks
- Can adapt to policy requirements
- Confidence levels can be enhanced simply by continued challenging of a user’s identity; it is not all or nothing
- Authenticates user and their device simultaneously
- Built from the bottom-up, so it works in tactical and DIL environments as well as enterprise cloud environments

